Genuine Caller or Not?
With Cyber Fraud expected to top $2tr by 2019, its imperative that Boards of Directors define their Cyber strategy to best secure and protect confidential customer data.
Through social engineering tactics, criminals are scanning Facebook, Twitter, LinkedIn and other social media sites to gather sufficient information to build and complete personal profiles.
Trading personal information, i.e. date of birth, mothers maiden name, home address, social security numbers etc., is lucrative and paves the way for criminals to target the financial services sector and steal money from bank accounts by spoofing helpful call centre agents who innocently authenticate the caller based on the credible information obtained.
Caller Authenticity

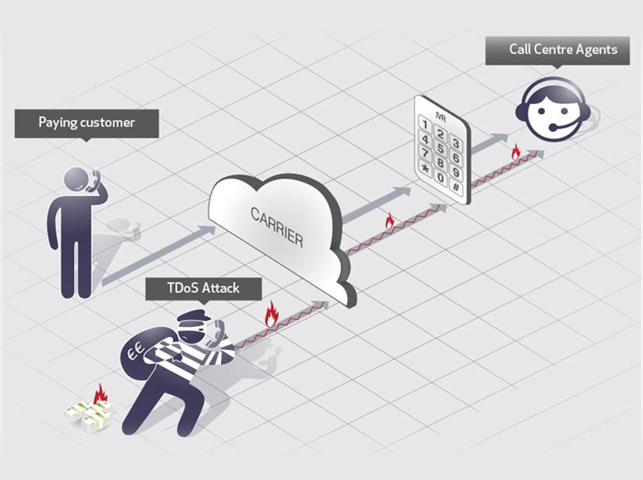
UC Defence protects call centre agents and back office employees from nuisance callers who are motivated to extort money, steal confidential data or disrupt this critical infrastructure. Caller Authentication techniques from UC Defence are to UC security as IDS/ IPS/ NAT are to ICT security. The solution highlights are as follow:
- Identify calls as genuine, nuisance or machine
- Reject suspicious call origins by monitoring Caller ID and ANI
- Audio Captcha via in-built IVR
- Comprehensive Black/ White List Policies
- Active Directory Integration

Caller Authentication
UC Defence provides a flexible automated IVR (interactive voice response) service where incoming callers self-authenticate by interacting with customer information systems and databases. Authenticated callers will be successfully transferred to call centre agents, while unsuccessful callers will be re-routed or denied entry to the UC environment.
Our IVR self-authentication application is secure and flexible, providing the client with the necessary integration to tailor their qualification criteria to meet their needs
