Toll Fraud
Toll Fraud or IRSF (international revenue share fraud) continues to be a global scourge, now greater than credit card fraud and estimated to be costing the global business community in excess of $8bn per annum.
Hacktivists commit this fraud by accessing the telephone lines and calling premium rate number services, their motivation stems from the lucrative profits that are generated from owning these premium rate numbers.
Unsecured access routes such as DDI numbers provide the hackers with direct access to the UC solution, thereafter they seek to exploit end user security via digital cyber tools such as war diallers. A successful breach means the hackers have accessed dial tone, after which they generate as many calls as possible to their premium rate – revenue share numbers.
Toll Fraud attacks generally occur during the weekend when the enterprise is unmanned, the victims are usually informed on Monday morning from their service provider that their UC infrastructure has been compromised. Average incident value is $30,000 and the victims are liable.
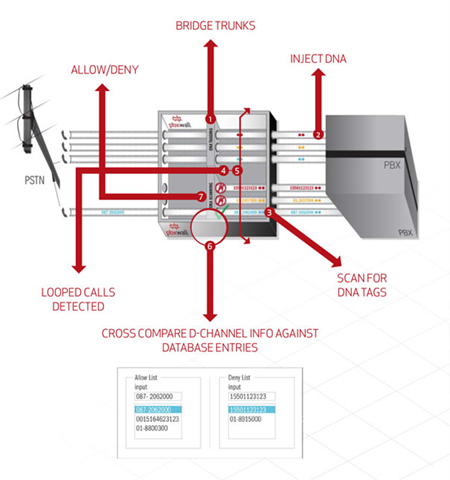
As illustrated in the infographic below, unsecured access routes such as DDI numbers provide the hackers with direct access to the UC platform, thereafter they seek to exploit end user security credentials via digital cyber tools such as war diallers. A successful breach means the hackers have accessed dial tone, after which they generate as many calls as possible to their premium rate – revenue share numbers.

Utilising an Innovative Technique, UC Defence combats the threat of Toll Fraud at it Very Core:
- Our technology consists of a back-to-back user agent
application which has the ability to automatically inject
traceable watermarks into every inbound call that enters the
UC infrastructure. - In real-time, our application continually scans all outbound
calls for the purpose of detecting watermarks. - In default mode, UC Defence will block all outbound calls containing watermarks, except
for situations where the “called number” was previously entered within the allow/deny database