UC Defence Mitigation Techniques
UC Defence has developed novel and innovative voice firewalls, our intellectual property was designed to automatically detect and block the following cyber crimes:
- Toll Fraud
- Vishing
- TDoS
- Eavesdropping
UC Defence protects both ISDN and SIP trunks from the aforementioned crimes.
Real Time Detection & Blocking
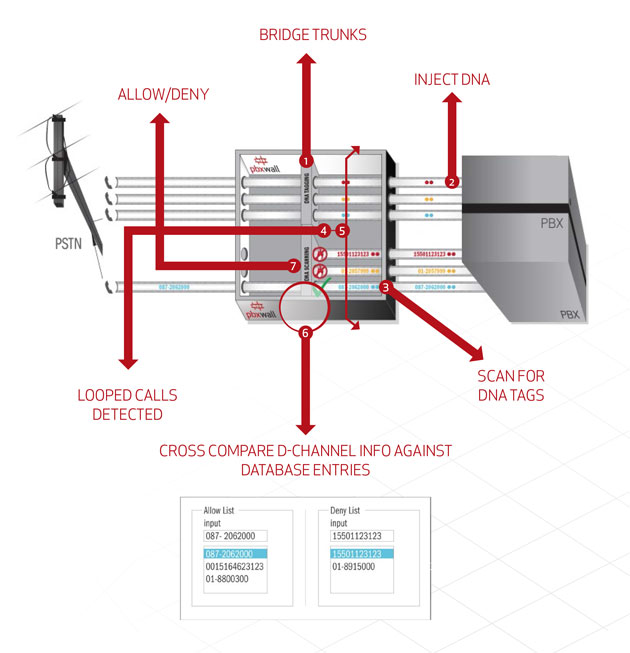
UC Defence is a back to back user agent that bridges the active trunk circuits that integrate to telephony infrastructures such as UC, Contact Centre or PBX. Our real time detection and blocking technique combats the crime of Toll Fraud at its very core. The solution highlights are as follows:
- UC Defence is a back to back user agent that injects a unique Watermarking Digital Data Stream into the Audio Channel or RTP Media Stream on all inbound calls
- Continually scans all outbound calls for the purpose of detecting Watermarks
- Detection of a watermark confirms that a call was looped through the UC Network/ PBX, i.e. “dial-through, call divert”
- Automatically terminates all looped calls unless the called number is already white listed
- Supports comprehensive black list policy
- Logs and distributes alerts for all events
- Continually protects, 24x7x365
Caller Validation
Along our journey to commercialize UC Defence, we engaged with international resellers, heads of ICT and security, to further develop our services to protect critical infrastructure from other cyber threats such as TDoS (telephony denial of service), vishing and eavesdropping.:
Our Caller Validation techniques are to UC security as IDS, IPS and NAT are to data network security. The solution highlights are as follow:
- Automatically identifies calls that are genuine, nuisance or machine
- Onward routes all white list entries
- Rejects all black list entries
- IVR Caller Validation process for non-white/ black list entries
- Onward routes all validated calls (alternative routing options)
- Terminates non-validated callers
- Supports comprehensive black list policy
- Logs and distributes alerts for all events
- Continually protects, 24x7x365
Technology Benefits
Unlike existing re-active policy based solutions, UC Defence insures that all fraudulent call activity is automatically detected and blocked.